As the majority of our courses are still online, we wanted to have a refresh on best practices for Zoom, you can see our main Zoom help page here. This post will focus on how to ensure your Zoom virtual classroom sessions remain secure.
The overwhelming majority of Zoom courses in the fall semester were conducted online with no significant security issues. However, there were a few unfortunate incidents of “Zoom bombing” where an unauthorized user gained access to and disrupted classes in progress.
This tech tip will review the best security practices to ensure that your course stays as secure as possible and you experience no interruption. Please also review the CUNY Zoom security protocol.
Enable security features
To enable these security features in your account, go to https://cuny.zoom.us . Enter your CUNY username and password (ie: John.Doe89@login.cuny.edu), if you have any difficulty logging in, please contact support@qc.cuny.edu.
- Click “Settings” on the left sidebar.
- Click “Security.”
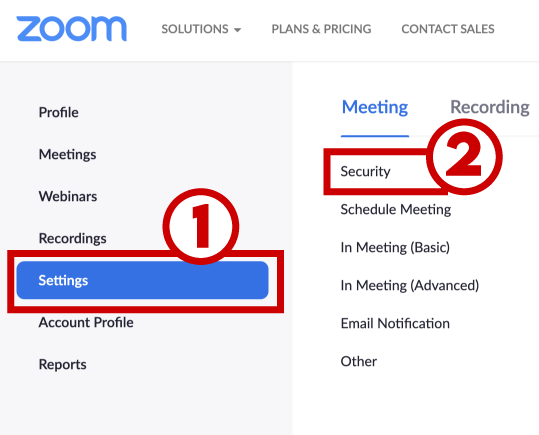
How to require users to authenticate
Once you are in “security” (see above):
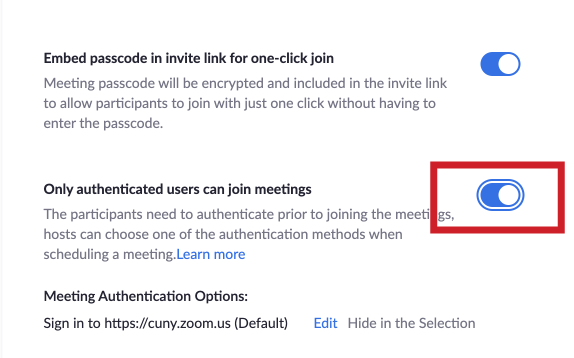
- Scroll down to a setting called “Only authenticated users can join meetings.”
- Slide the button to the right so it turns blue (if it is already blue, it has already been enabled).
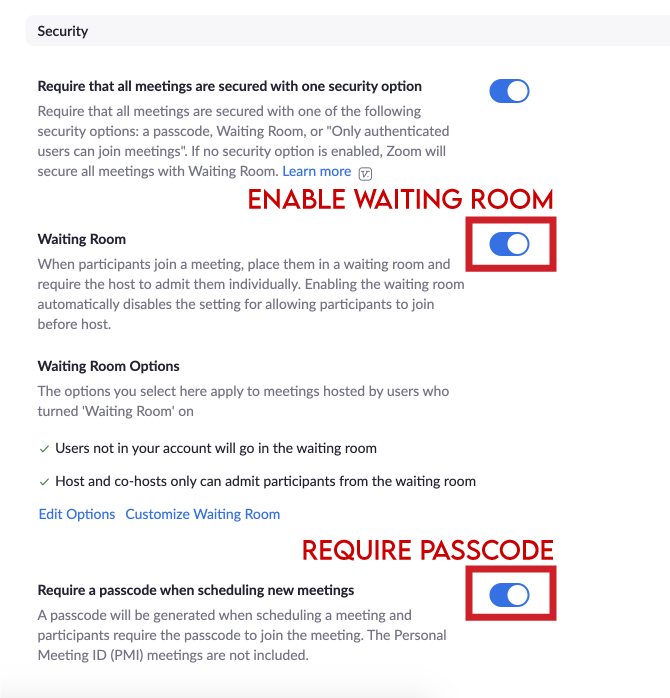
Enable the Waiting Room and Passcode in the Web Interface
Move the “Waiting Room” and “Require a Passcode when scheduling new meetings” buttons to the right until they turn blue. If these buttons are already blue, the Waiting Room and Passcode are already enabled.
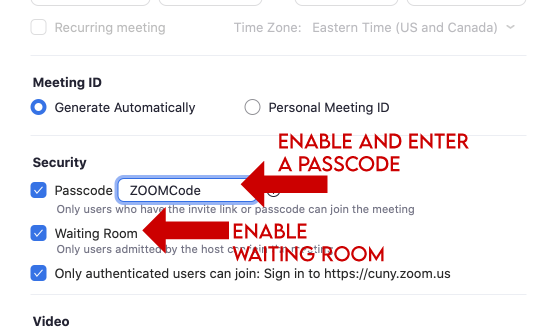
Enable Passcode and Waiting Room in the Desktop App
Under “Schedule Meeting”
- Enable the Passcode option and enter a passcode in the field.
- Enable the Waiting Room option.
Locking the room
The Zoom session can be locked while in progress, preventing any additional users from accessing the class. After the “lock” is enabled, any additional attempts to access the session will automatically be rejected. This can prevent bad actors, but it also means legitimate students who have technical difficulties in the middle of the session or lose connection will be unable to rejoin. It is for this reason we don’t recommend enabling this feature unless you have significant issues with Zoom bombing. This feature can only be enabled once the Zoom class is in progress.
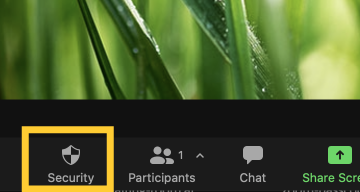
- To Lock the room, click “Security” on the Zoom control panel (usually located at the bottom of the screen)

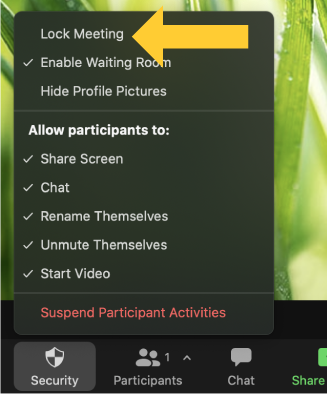
- Click “Lock Meeting” in the resulting pop-up menu.

As none of these features in isolation will prevent Zoom issues in their entirety, please use a combination of the above security measures. Bear in mind, however, no matter how secure you aim to be, there will be people who try to circumvent your efforts. These security measures, especially requiring users to authenticate through zoom will significantly reduce Zoom issues, and if they do occur, make it easier to identify the responsible party.
For that reason, please see below for the procedures of reporting a Zoom incident.
Reporting Zoom bombing
If you encounter a Zoom bomber during your class, you can remove them from the session and “lock” the room so they are unable to reenter. Be aware that if a student has an issue and needs to get back in the lock will prevent them from doing so. Make sure a reentry protocol is established (ie: you will have your email open if a student needs to contact you for class issues) prior to the session.
How to report Zoom bombing
Document the time, name, and whatever other information you have on the bad actor including the disruptive nature of their actions. You can retrieve detailed information on all users in your session in your CUNY Zoom site.
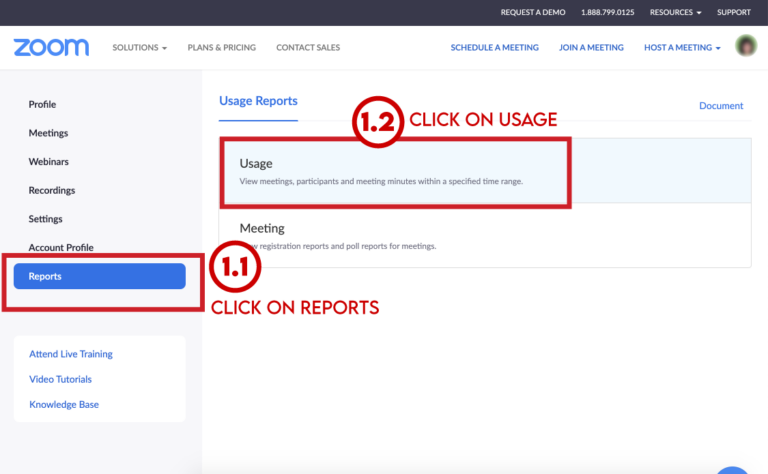
- Click on Reports in the left side menu
- Click on Usage under Usage Reports->Usage.

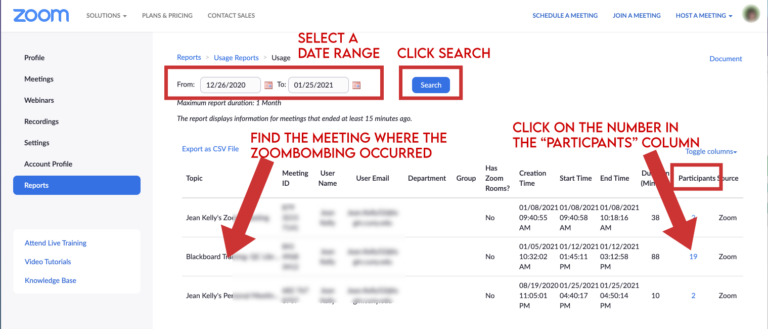
- Adjust the date range settings so that the date the incident occurred is shown. Click on the number in the Participants column. This brings up a list of participants with their start time, email address, and username.

- Meeting Participants will show the CUNY login of the user in question if you have enabled “Require users to authenticate.”
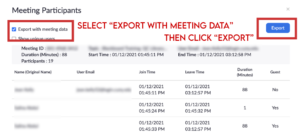
- Take a screenshot of the Zoom bomber’s information (including which user it was and when the incident occurred), or select “Export with Meeting data” then click “Export” to download the report as a CSV file.

- Report this information to Office of Public Safety at security@qc.cuny.edu or 718-997-5912 and the Office of Vice President for Student Affairs at VPSA@qc.cuny.edu or 718-997-5500. Be sure to include the documentation of the log of the incident, specifying the user and the time the Zoom bombing occurred.